|
|
|
.NET OBFUSCATION by ARVIND RAMAIYA
This is my take
of Obfuscation in .NET as compared to Java.
The following links were used to research the
process of Obfuscation, the tools available
http://www.cs.arizona.edu/~collberg/Research/Obfuscation/Resources.html
An introduction
to the .NET framework – some techie stuff
The .NET architecture is composed of the Common
Language Runtime, the VM in .NET world which compiles code into Intermediate
Language and IL into binaries. The .NET Framework 1.1 has been built on xml,
assembly manifest information are stored in this
format along with the assemblies themselves. This makes the above reverse
engineering process trivial and makes distribution of .NET code an issue in the
industry. There is a Common Language Runtime which has a number of engines
including the metadata engine which generates metadata to be stored along with
the assembly. The compiler generates the IL along with metadata, which is data about
data. It tells the runtime more about the code, such as the definition of each
type, signatures, type libraries, registry entries and other extra information.

Figure showing the basic
compile process in Java or .NET
The problem with writing code in a language which
sits behind a VM that interprets the code written into an abstract language, is the security hole it generates. Reverse
engineering becomes easy from the abstract language to the source code as is
shown in the figure below.
Obfuscation – the process
Obfuscation
is the process of preventing re-engineering by converting the bytecodes in Java
or IL .NET to Obfuscated code which is then interpreted into a binary, which
cannot be reverse engineered.
Just
like java programs are compiled using javac.exe before being executed using the
java VM java.exe .NET programs are also interpreted twice.
Obfuscators – the tool
Obfuscators, which automatically
transform a program by code obfuscation, are more and more available on the
Internet by the increasing requirement. Various obfuscators provide different
security levels to protect .NET programs or IL code. Some Java obfuscators
change the compiled class to various names that, when decompiled, follow
illegal syntax and as such can't be recompiled. Others simply change names.
Many Java obfuscators remove extraneous symbolic information used to decompile
the class.
Some of the most common and used .NET Obfuscators
are LSW Dotnet IL Obfuscator, Demeanor
for .NET, .NET IL-Obfuscator, Salamander .NET Obfuscator
.NET framework provides you with 2 tools to
assemble and disassemble; Intermediate Language Assembler and Intermediate
Language Disassembler.
The tool used to demonstrate Obfuscation is the LSW
.NET IL Obfuscator.
The two instances of the IL code are shown, and the
process of using ILASM.exe to re-assemble IL into source code has been show
Before Obfuscation
C:\arvind>ilasm ReadingXml.il

Microsoft (R) .NET Framework IL
Assembler. Version 1.0.3705.0
Copyright (C) Microsoft Corporation 1998-2001. All
rights reserved.
Assembling 'ReadingXml.il' , no listing file,
to EXE --> 'ReadingXml.EXE'
Source file is UTF-8
Assembled method Form1::.ctor
Assembled method Form1::Dispose
Assembled method Form1::InitializeComponent
Assembled method Form1::Main
Assembled method Form1::btnReadXML_Click
Assembled method Form1::btnShowSchema_Click
Creating PE file
Emitting members:
Global
Class 1 Fields: 6; Methods: 6;
Resolving member refs: 51 -> 51 defs, 0 refs
Operation completed
successfully
After
Obfuscation
C:\arvind\rep>ilasm obfuscate.il
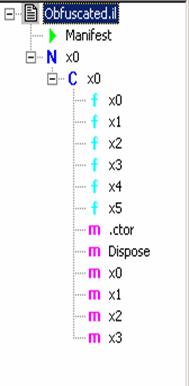
Microsoft (R) .NET Framework IL
Assembler. Version 1.0.3705.0
Copyright (C) Microsoft Corporation 1998-2001. All
rights reserved.
Assembling 'obfuscate.il' , no listing file,
to EXE --> 'obfuscate.EXE'
Source file is ANSI
obfuscate.il(3) : error : syntax error
at token '´' in: ´╗┐
***** FAILURE *****